How to Hack a Webserver
Customers usually address the web to urge information and buy products and services. Towards that end, most organizations have websites. Most websites store valuable information like MasterCard numbers, email addresses, and passwords, etc. This has made them targets to attackers. Defaced websites also can be wont to communicate religious or political ideologies etc.
In this tutorial, we’ll introduce you to web servers hacking techniques and the way you’ll protect servers from such attacks.
Web server vulnerabilities
A web server may be a program that stores files (usually web pages) and makes them accessible via the network or the web . an internet server requires both hardware and software. Attackers usually target the exploits within the software to realize authorized entry to the server. Let’s check out a number of the common vulnerabilities that attackers cash in of.
* Default settings–
These settings like default user id and passwords are often easily guessed by the attackers. Default settings may additionally allow performing certain tasks like running commands on the server which may be exploited.
*Misconfiguration of operating systems and networks –
certain configurations like allowing users to execute commands on the server are often dangerous if the user doesn’t have an honest password.
* Bugs within the OS and web servers–
Discovered bugs within the OS or web server software also can be exploited to realize unauthorized access to the system.
In addition to the above-mentioned web server vulnerabilities, the subsequent also can lead to unauthorized access
* Lack of security policy and procedures–
Lack of a security policy and procedures like updating antivirus software, patching the OS and web server software can create security loopholes for attackers.
Types of Web Servers The following may be a list of the common web servers:
a)Apache:
This is often the commonly used web server on the web. it’s cross-platform but is it’s usually installed on Linux. Most PHP websites are hosted on Apache servers.
b)Internet Information Services (IIS)–
It is developed by Microsoft. It runs on Windows and is that the second most used web server on the web. Many asp and aspx websites are hosted on IIS servers.
c)Apache Tomcat –
Most Java server pages (JSP) websites are hosted on this sort of web server.
* Other web servers –
These encompass Novell’s Web Server and IBM’s Lotus Domino servers.
Types of Attacks against Web Servers
* Directory traversal attacks–
This type of attack exploits bugs within the webserver to realize unauthorized access to files and folders that aren’t within the property right. Once the attacker has gained access, they will download sensitive information, execute commands on the server, or install malicious software.
* Denial of Service Attacks–
With this sort of attack, the online server may crash or become unavailable to legitimate users.
* Domain name System Hijacking –
With this sort of attacker, the DNS setting is changed to point to the attacker’s web server. All traffic that was alleged to be sent to the online server is redirected to the incorrect one.
* Sniffing–
Unencrypted data sent over the network could also be intercepted and wont to gain unauthorized access to the online server.
* Phishing–
With this sort of attack, the attack impersonates the websites and directs traffic to the fake website. Unsuspecting users could also be tricked into submitting sensitive data like login details, MasterCard numbers, etc.
* Pharming–
With this type of attack, the attacker compromises the name System ( DNS) servers or on the user computer in order that traffic is directed to a malicious site.
* Defacement–
With this sort of attack, the attacker put back the corporation’s website with a special page that contains the hacker’s name, images and should include background music and messages.
Effects of successful attacks
* An organization’s reputation is often ruined if the attacker edits the web site content and includes malicious information or links to a porn website.
* The online server is often wont to install malicious software on users who visit the compromised website. The malicious software downloaded onto the visitor’s computer is often an epidemic, Trojan or Botnet Software, etc.
* Compromised user data could also be used for fraudulent activities which can cause business loss or lawsuits from the users who entrusted their details with the organization.
Web server attack tools
Some of the regular web server attack tools include;
*Metasploit–
This is often an open-source tool for developing, testing and using exploit code. It is often wont to discover vulnerabilities in web servers and write exploits which will be wont to compromise the server.
*MPack–
This is often an internet exploitation tool. it had been written in PHP and is backed by MySQL because of the database engine. Once an internet server has been compromised using MPack, all traffic thereto is redirected to malicious download websites.
*Zeus–
This tool is often wont to turn a compromised computer into a bot or zombie. A bot may be a compromised computer that is employed to perform internet-based attacks. A botnet may be a collection of compromised computers. The botnet can then be utilized in a denial of service attack or sending spam emails.
*Neosplit –
This tool is often wont to install programs, delete programs, replicating it, etc.
How to avoid attacks on Webserver
An organization can adopt the subsequent policy to guard itself against webserver attacks.
* Patch management– this involves installing patches to assist secure the server. A patch is an update that fixes a bug within the software. The patches are often applied to the OS and therefore the webserver system.
* Secure installation and configuration of the OS
* Secure installation and configuration of the online server software
* Vulnerability scanning system– these include tools like Snort, NMap, Scanner Access Now Easy (SANE)
* Firewalls are often wont to stop simple DoS attacks by blocking all traffic coming the identify source IP addresses of the attacker.
* Antivirus software are often wont to remove malicious software on the server
* Disabling Remote Administration
* Default accounts and unused accounts must be faraway from the system
* Default ports & settings (like FTP at port 21) should be different to custom port & settings (FTP port at 5069)
Hacking Activity: Hack a WebServer
In this practical scenario, we are getting to check out the anatomy of an internet server attack. we’ll assume we are targeting www.techpanda.org. We aren’t actually getting to hack into it as this is often illegal. we’ll only use the domain for educational purposes.
What we’ll need
* A target www.techpanda.org
* Bing program
* SQL Injection Tools
* PHP Shell, we’ll use DK shell http://sourceforge.net/projects/icfdkshell/
Information gathering
We will get to get the IP address of our target and find other websites that share an equivalent IP address.
We will use a web tool to seek out the target’s IP address and other websites sharing the IP address
*Enter the URL https://www.yougetsignal.com/tools/web-sites-on-web-server/ in your browser
*Enter www.techpanda.org because the target

Click on Check button
You will get the subsequent results
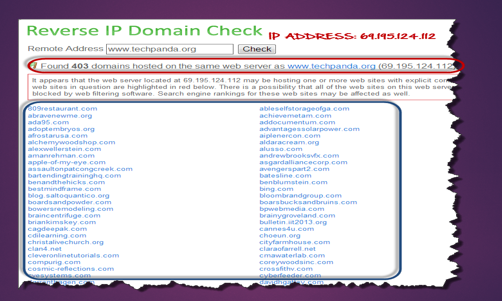
Based on the above outcomes, the IP address of the target is 69.195.124.112
We also acknowledged that there are 403 domains on an equivalent web server.
Our next step is to scan the opposite websites for SQL injection vulnerabilities. Note: if we will find a SQL vulnerable on the target, then we might directly exploit it without considering other websites.
* Enter the URL www.bing.com into your browser. this may only work with Bing so don’t use other search engines like google or yahoo
* Enter the subsequent search query
IP:69.195.124.112 .php?id=
HERE,
* “IP:69.195.124.112” limits the search to all or any the online sites hosted on the webserver with IP address 69.195.124.112
You will get the subsequent results

As you’ll see from the above results, all the websites using GET variables as parameters for SQL injection are listed.
The next logical step would be to scan the registered websites for SQL Injection vulnerabilities. you’ll do that using manual SQL injection or use tools listed during this article on SQL Injection.
Uploading the PHP Shell:
We will not scan any of the websites listed as this is often illegal. Let’s assume that we’ve managed to login to one among them. you’ll need to upload the PHP shell that you simply downloaded from http://sourceforge.net/projects/icfdkshell/
* Unlock the URL where you uploaded the dk.php file.
* you’ll get the subsequent window.

* Clicking the Symlink URL will offer you access to the files within the target domain.
Once you’ve got access to the files, you’ll get login credentials to the database and do whatever you would like defacement, downloading data like emails, etc.