Worm, Virus & Trojan Horse: Ethical Hacking Tutorial
Some of the talents that hackers have are programming and computer networking skills. They often use these skills to realize access to systems. the target of targeting a corporation would be to steal sensitive data, disrupt business operations, or physically damage computer-controlled equipment. Trojans, viruses, and worms are often wont to achieve the above-stated objectives.
In this article, we’ll introduce you to a number of the ways in which hackers can use Trojans, viruses, and worms to compromise a computing system . we’ll also check out the countermeasures which will be wont to protect against such activities.
What is a Trojan horse?
A computer virus may be a program that permits the attack to regulate the user’s computer from a foreign location. The program is typically disguised as something that’s useful to the user. Once the user has installed the program, it’s the power to put in malicious payloads, create backdoors, install other unwanted applications which will be wont to compromise the user’s computer, etc.
The list below shows a number of the activities that the attacker can perform employing a computer virus:
*Use the user’s computer as a part of the Botnet when performing distributed denial of service attacks.
*Battering the user’s computer (crashing, blue screen of death, etc.)
*Stealing sensitive data like stored passwords, MasterCard information, etc.
*Modifying files on the user’s computer
*Electronic money stealing by performing unauthorized money transfer transactions
*Log all the keys that a user presses on the keyboard and sending the info to the attacker. This method is employed to reap user ids, passwords, and other sensitive data.
*Viewing the users’ screenshot
*Downloading browsing history data
What is a worm?
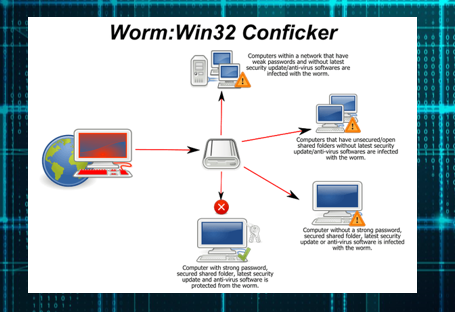
A worm may be a malicious computer virus that replicates itself usually over a network. An attacker may use a worm to accomplish the subsequent tasks;
*Install backdoors on the victim’s computers. The generated backdoor could also be wont to make zombie computers that are wont to send spam emails, perform distributed denial of service attacks, etc. the backdoors also can be exploited by other malware.
*Worms can also slow down the network by consuming the bandwidth as they replicate.
*Install harmful payload code carried within the worm.
What is a Virus?

*A virus may be a computer virus that attaches itself to legitimate programs and files without the user’s consent. Viruses can consume computer resources like memory and CPU time. The rushed programs and files are said to be “infected”. A bug could also be used to;
*Access private data like user id and passwords
*Display annoying messages to the user
*Corrupt data in your computer
*Log the user’s keystrokes
Computer viruses are known to use social engineering techniques. These techniques involve deceiving the users to open the files which appear to be normal files like Word or Excel documents. Once the file is opened, the virus code is executed and does what it’s intended to try to do.
Trojans, Viruses, and Worms countermeasures:

*To protect against such attacks, a corporation can use the subsequent methods.
*A policy that prohibits users from downloading unnecessary files from the web like spam email attachments, games, programs that claim to hurry up downloads, etc.
*Anti-virus software should be installed on all user computers. The anti-virus software must be updated frequently, and scans must be performed at specified time intervals.
*Scan auxiliary storage devices on an isolated machine especially people who originate from outside the organization.
*Regular backups of critical data must be made and stored on preferably read-only media like CDs and DVDs.
*Worms exploit vulnerabilities within the operating systems. Downloading OS updates can help reduce the infection and replication of worms.
*Worms also can be avoided by scanning, all email attachments before downloading them.